To design a secure Infrastructure, you must be wondering if we need help from a SRE (Site Reliability Engineer) or a DevOps Engineer who has background and knowledge in Networks and Security along with DevOps principles. These people come with technical expertise in designing a secure platform both On-Premise and on Cloud. However, with some basic knowledge about Networks you yourself can achieve a good network design without much help from your DevOps or SRE team.
To design a secure AWS Infrastructure we need to know the basics of VPC, Subnets, Route Tables, Security Groups, NAT Gateway and Internet Gateway. Using these technologies you can design a secure and efficient infrastructure for your platform. In this article, I’ll explain how an EC2 instance running in your VPC in a Private subnet reaches the internet.
To achieve this we need to make use of NAT (Network Address Translation) gateway and Internet Gateway, which helps to enable our EC2 instance running in private subnet to connect to Internet or other AWS services, but prevents the internet from initiating a connection with our instance. Following is the official AWS documentation we will be using to achieve this - https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-gateway.html
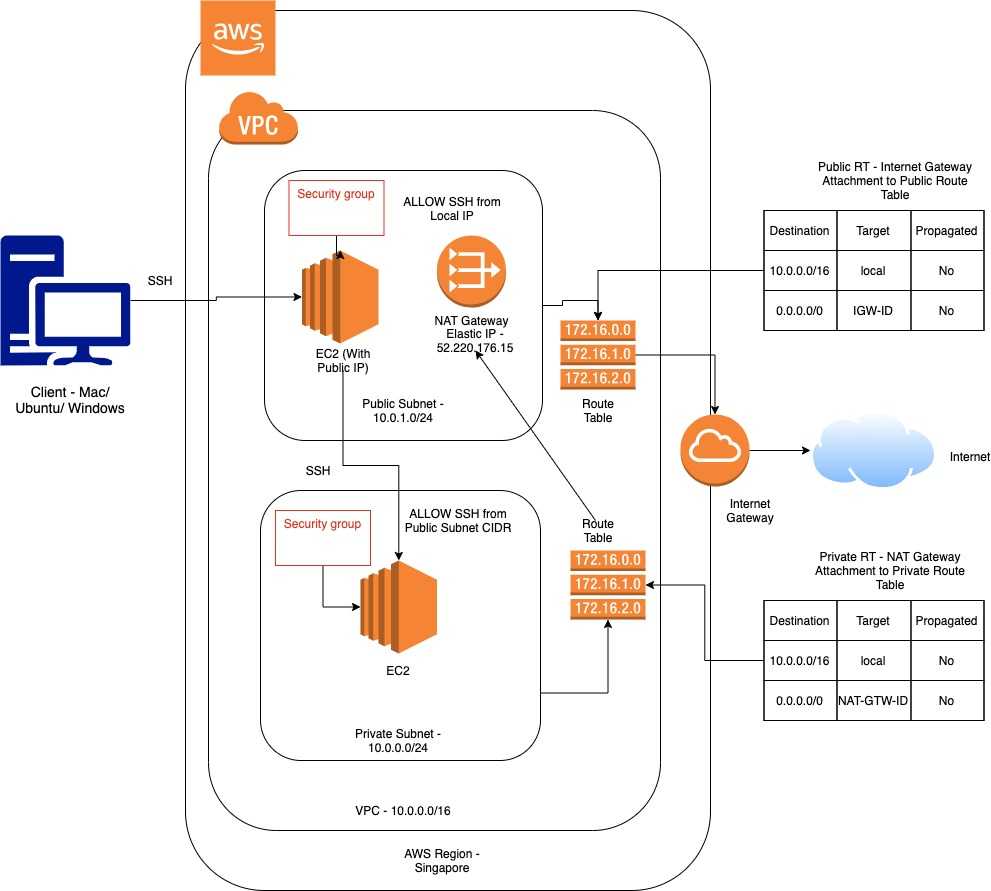
Architecture Diagram
Our AWS Infrastructure design will look something like this -
Now, let’s deep dive into the setup -
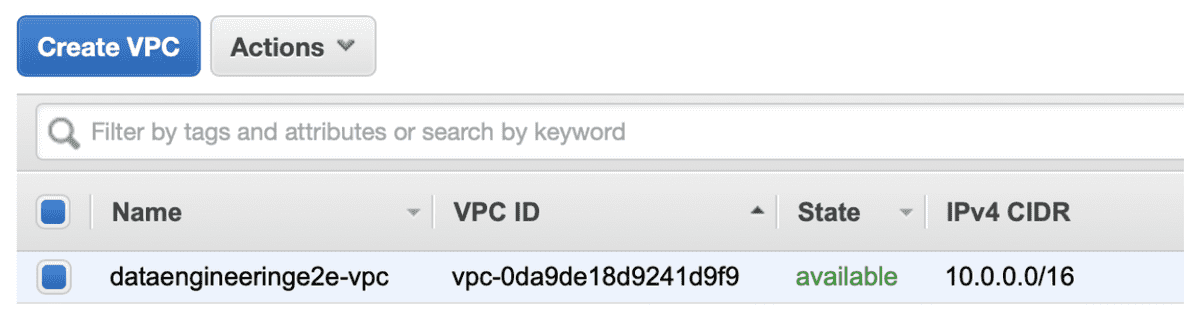
- Create a VPC
We need a Virtual Private Cloud setup in the AWS Account. In an organization ideally the CIDR range used by our VPC is provided by the SRE/ IT Networks team.
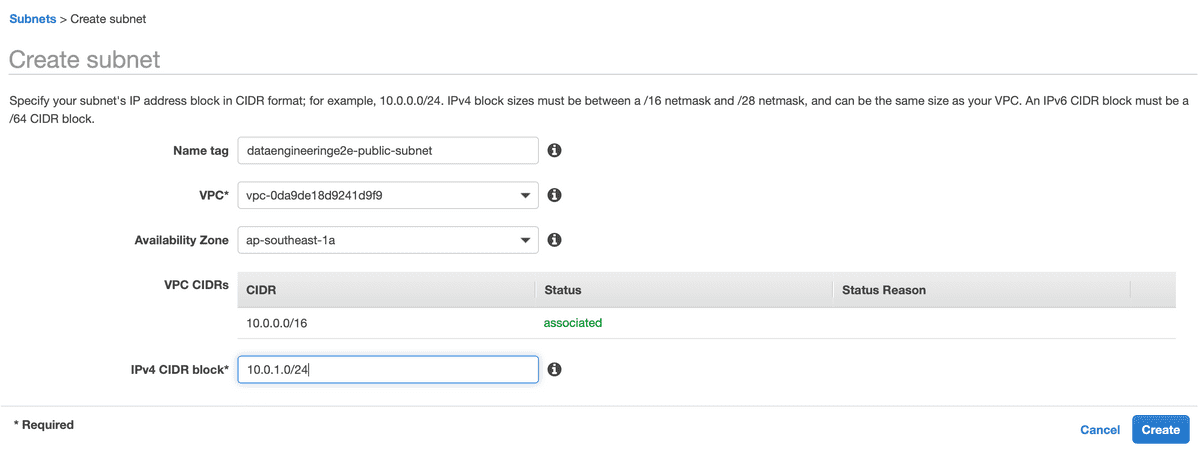
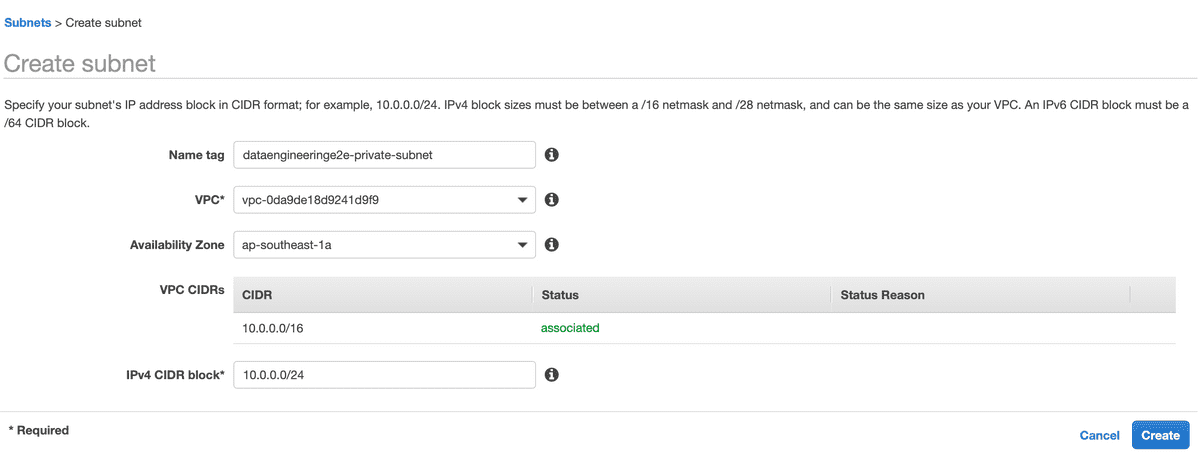
- Create a Public and Private Subnet
We need to create Public and Private subnets wherein we will setup our Bastion Host and EC2 instance respectively.
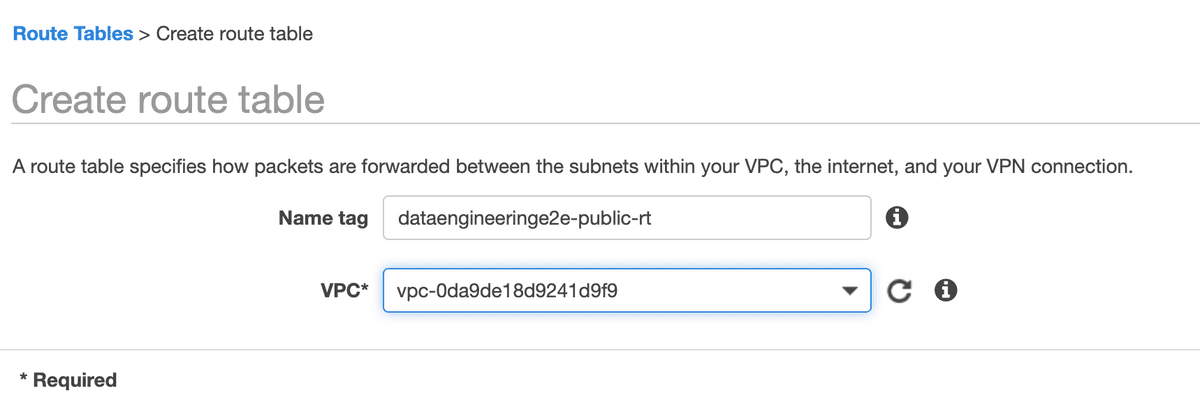
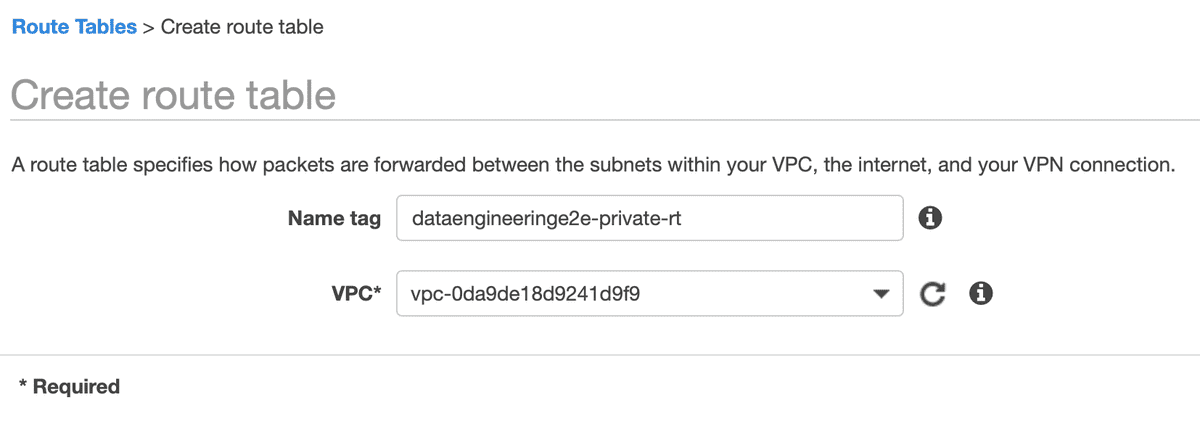
- Create Public and Private Route Table
Route tables are required for both subnets for route propagation. It’s a way to control network traffic movement.
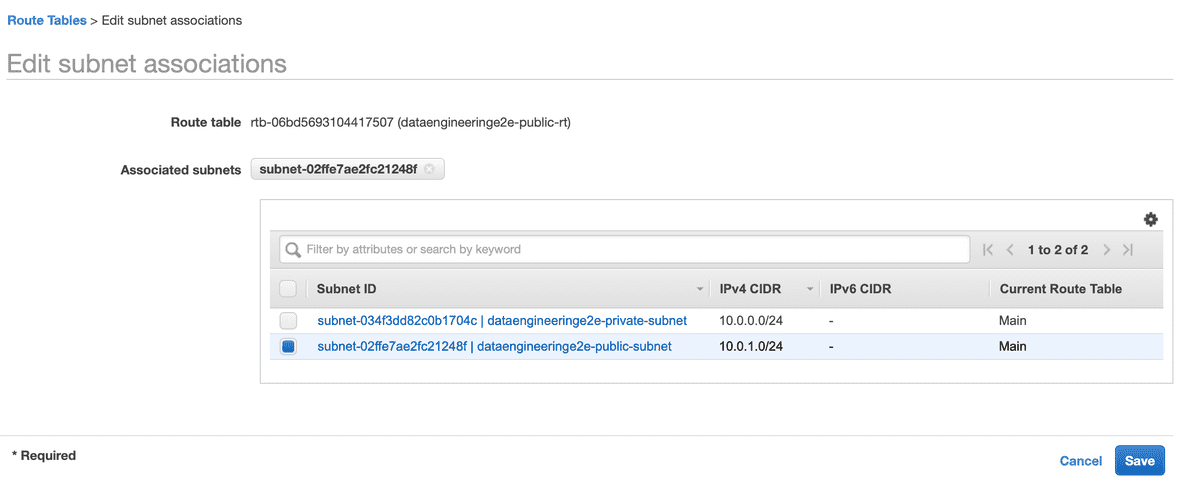
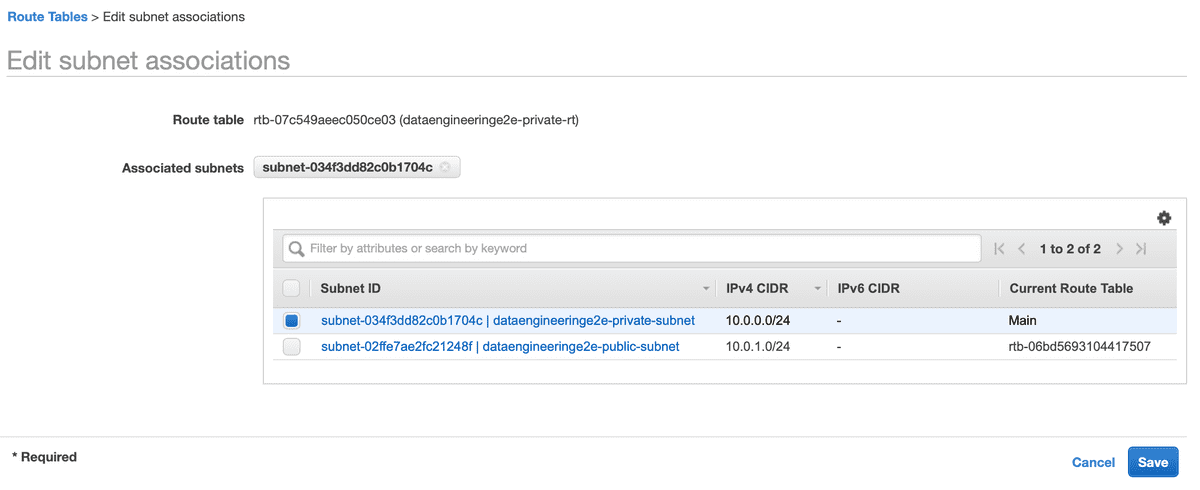
- Setup Route Table to Subnet Association
We need to now associate our Route Table with respective subnets.
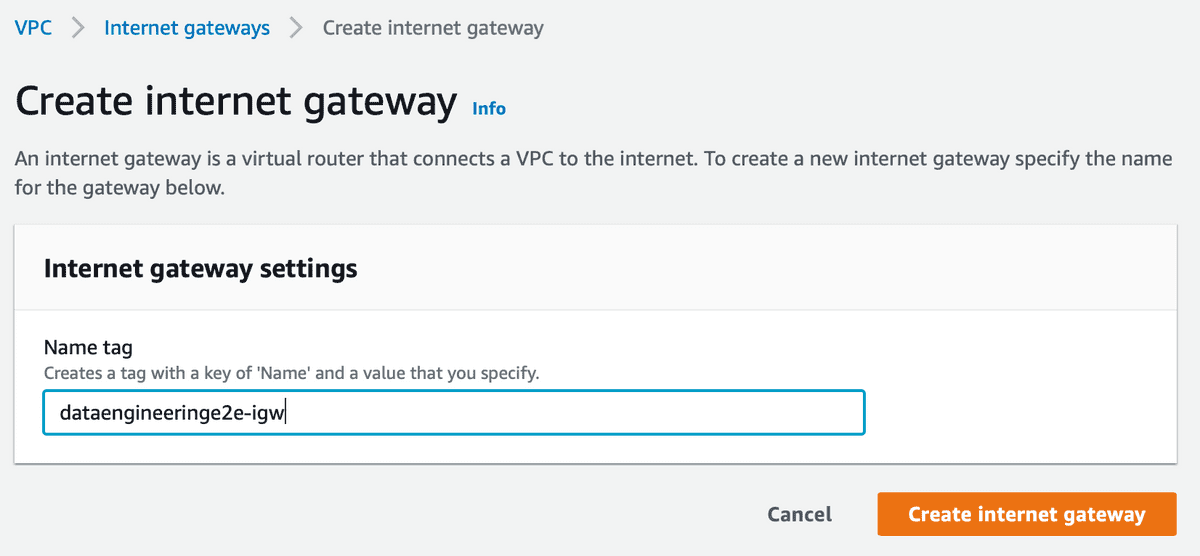
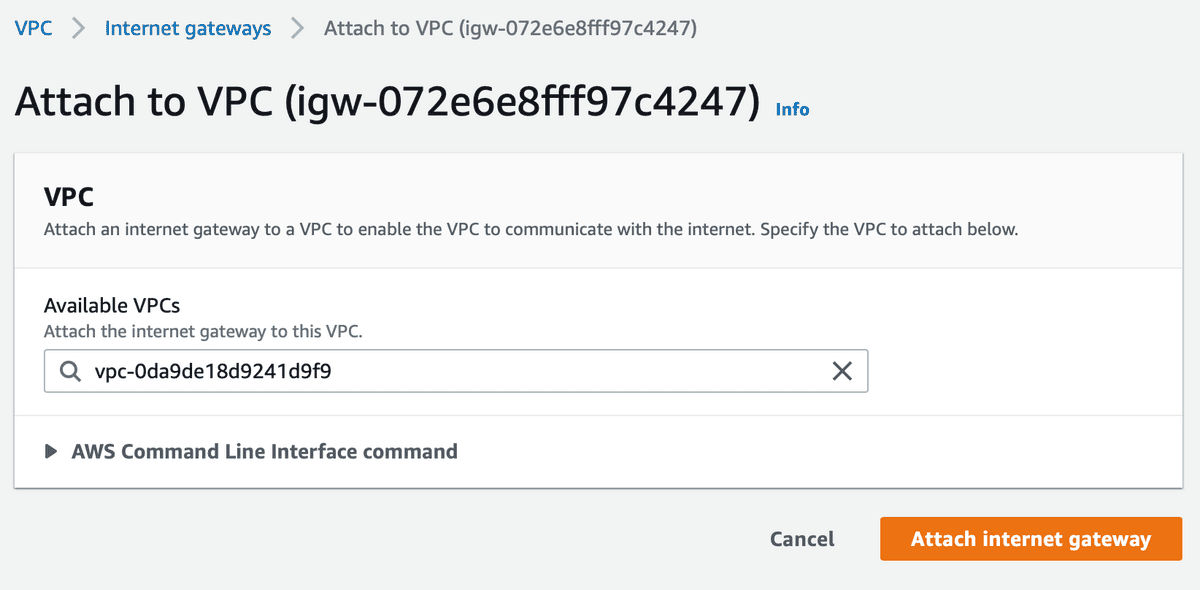
- Create an Internet Gateway and attach it to your VPC
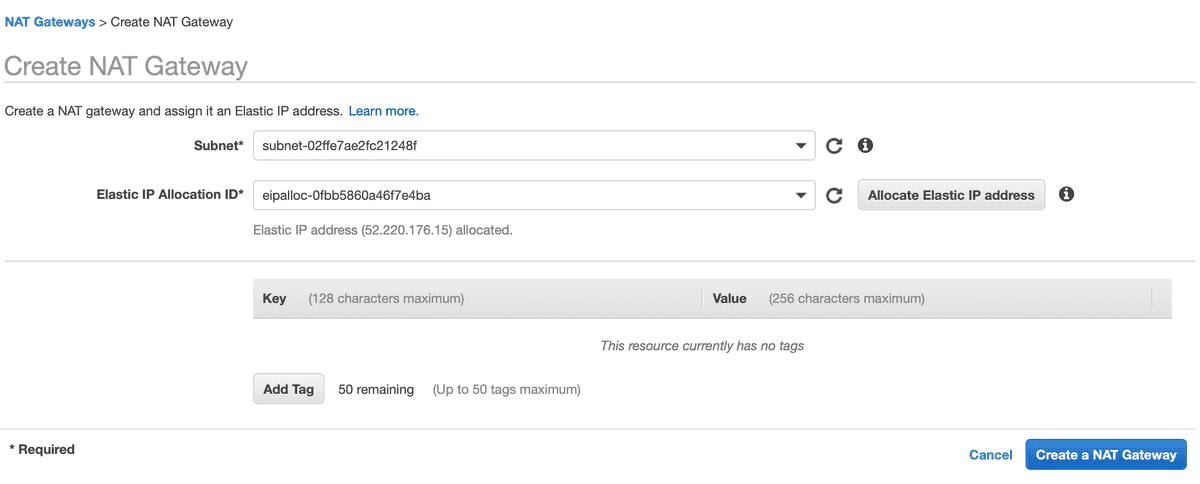
- Create a NAT Gateway and attach it to your Public Subnet
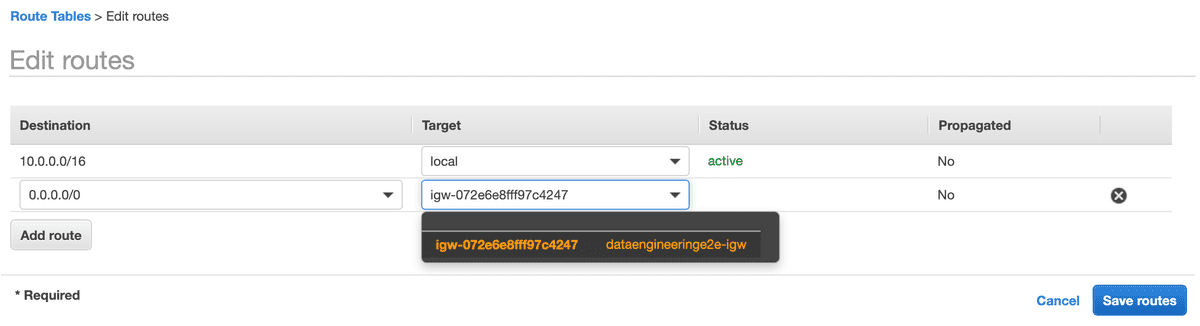
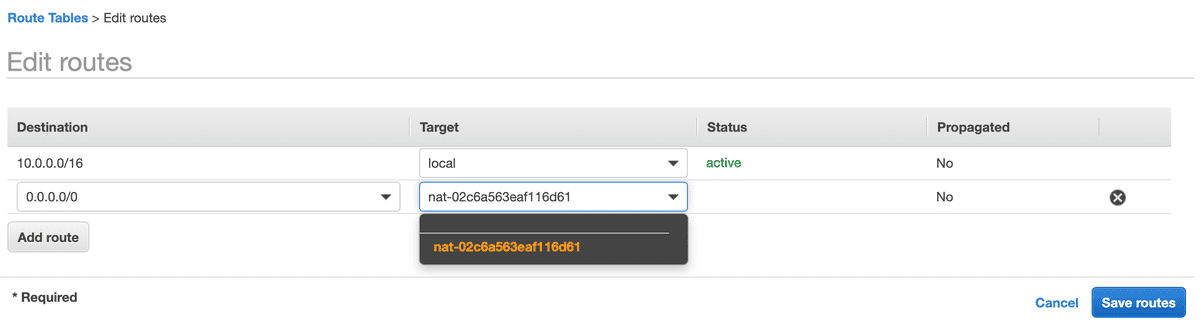
- Update Public Route Table with Internet Gateway Route
- Update Private Route Table with NAT Gateway Route
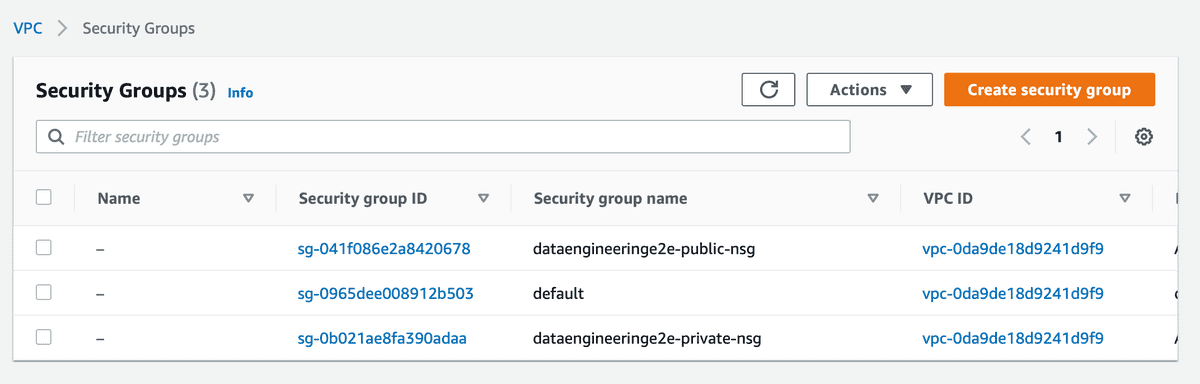
- Create Public and Private Network Security Group in your VPC
- Create a Key Pair
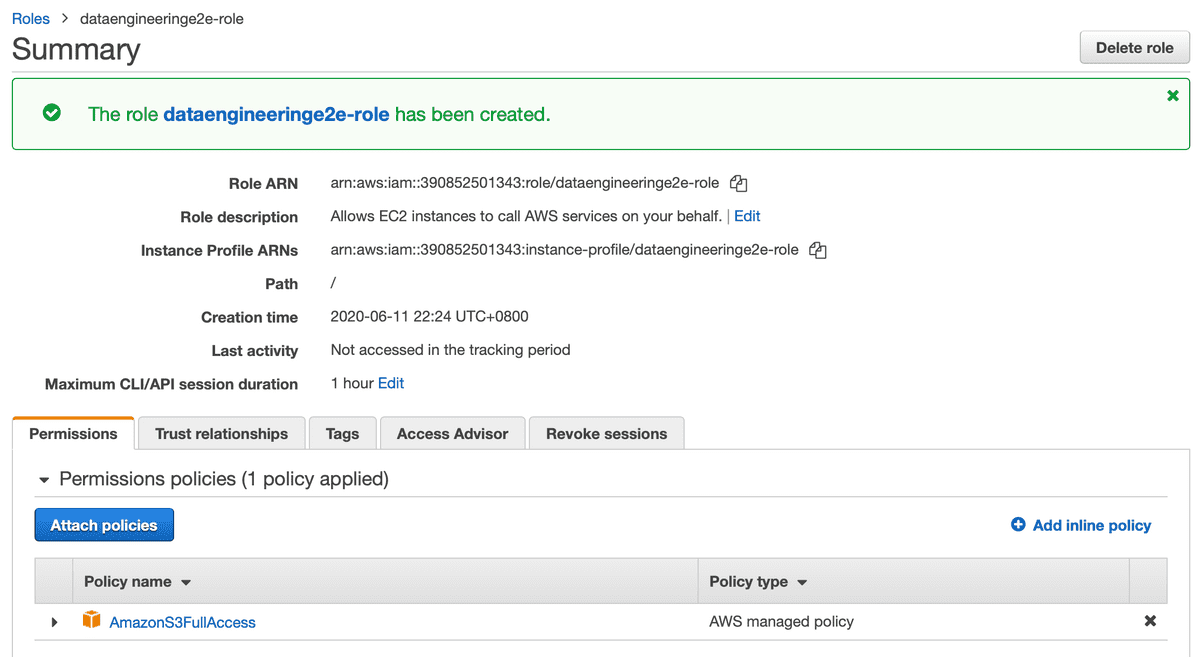
- Create an IAM Role
For this tutorial, I created a role with S3 access
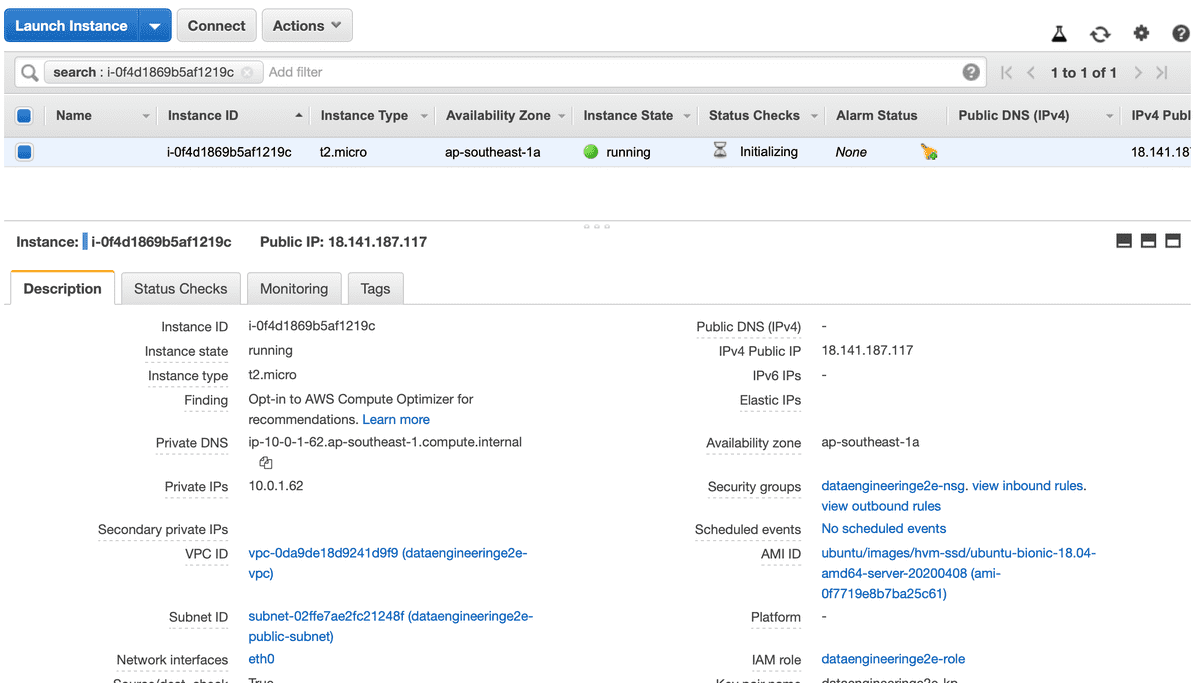
- Create an EC2 machine in Public Subnet
This EC2 machine will act as our Bastion Host
| AMI | Instance | VPC | Subnet | Role | Security Group | Key Pair |
| Ubuntu Server 18.04 LTS (HVM) | t2.micro | dataengineeringe2e-vpc | dataengineeringe2e-public-subnet | dataengineeringe2e-role | dataengineeringe2e-public-nsg | dataengineeringe2e-kp |
For Public Instance Enable Auto assign Public IP
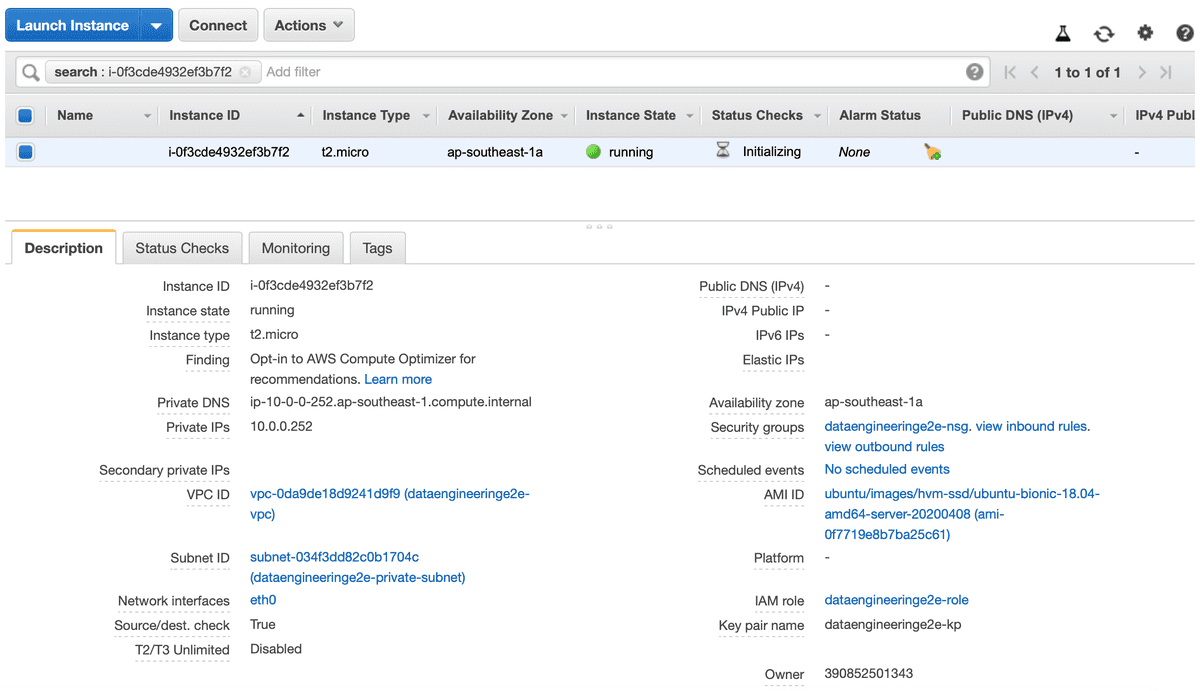
- Create an EC2 machine in Private Subnet
This EC2 machine will act as our test instance
| AMI | Instance | VPC | Subnet | Role | Security Group | Key Pair |
| Ubuntu Server 18.04 LTS (HVM) | t2.micro | dataengineeringe2e-vpc | dataengineeringe2e-private-subnet | dataengineeringe2e-role | dataengineeringe2e-private-nsg | dataengineeringe2e-kp |
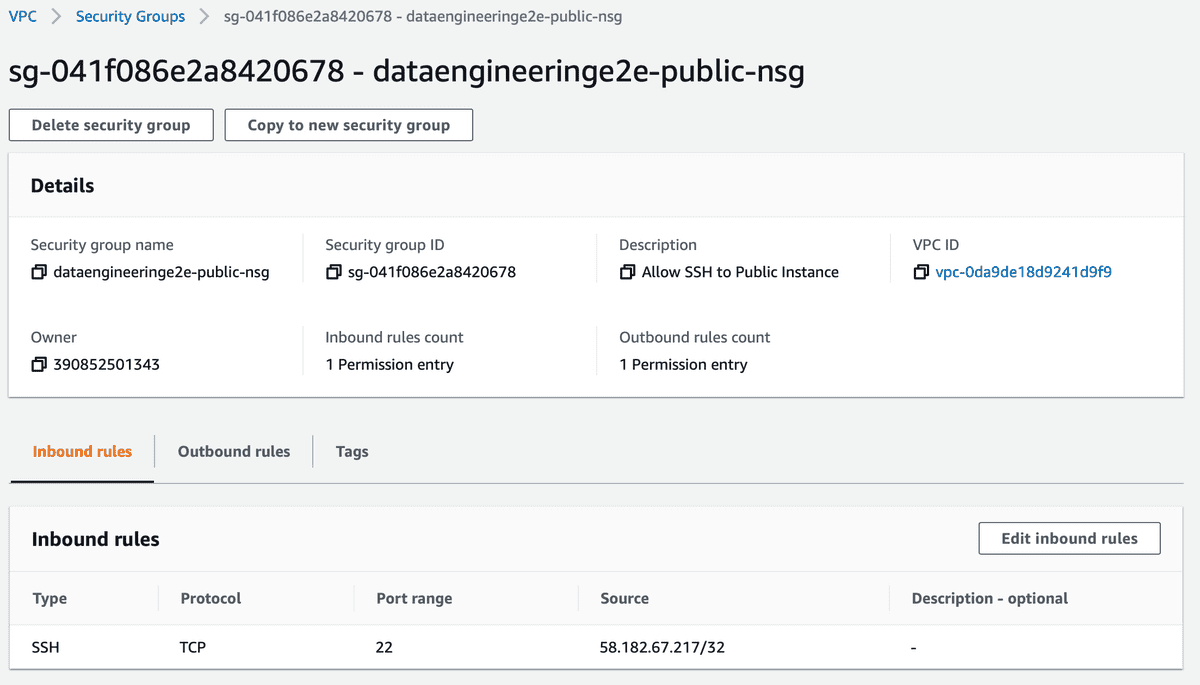
- Add Inbound Rule into Public Security Group to allow SSH from Local Computer
Check your IP - http://checkip.amazonaws.com
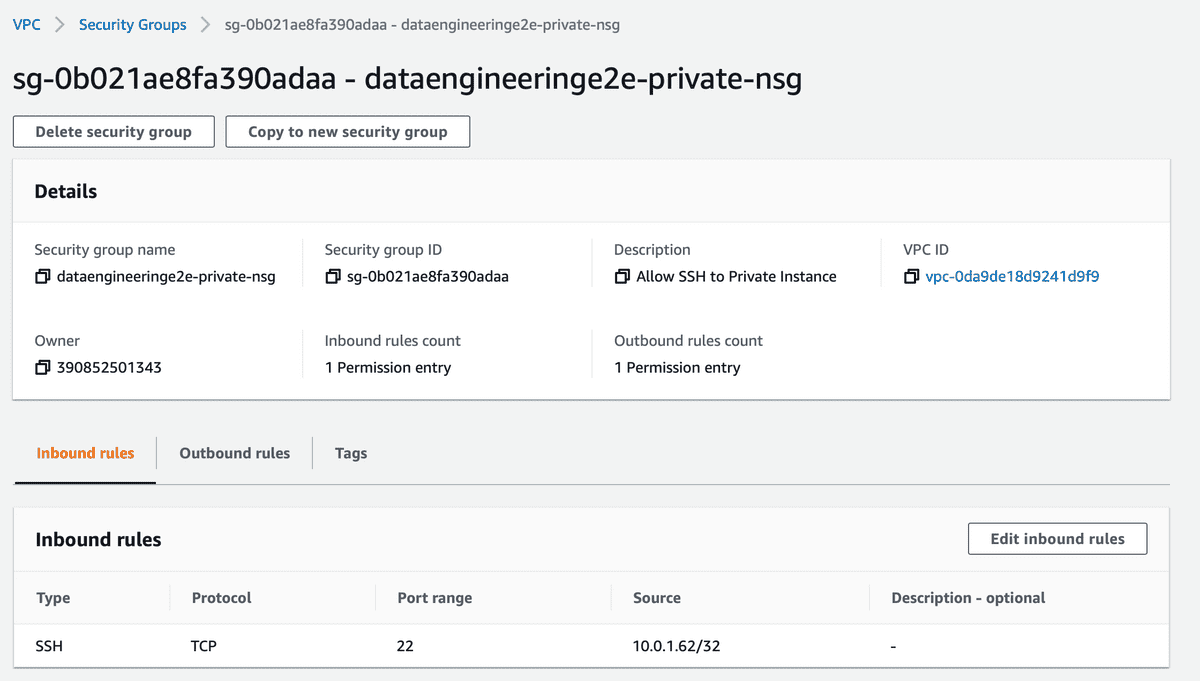
- Add Inbound Rule into Private Security Group to allow SSH from Public Subnet/ Public Instance
You can whitelist any of following things for this -
- Entire Public Subnet CIDR
- Private IP of Public EC2 machine
- Security Group of Public Subnet
- SSH into Public EC2 machine
- Change permissions to 400 on key pair
- SSH into the Public EC2 using Public IP
Try installing awscli
ubuntu@ip-10-0-1-62:~$ sudo apt-get update ubuntu@ip-10-0-1-62:~$ sudo apt install awscli ubuntu@ip-10-0-1-62:~$ aws s3 ls 2020-04-07 13:21:47 dataengineeringe2eSetup Key Pair on Public EC2 and try to connect to Private EC2 from it as
- Finally, we’re logged into the private instance. You can test, we’re able to reach the internet from a Private EC2 machine in a safe and secure manner.
In organizations instead of using a Bastion Host, ideally we use a VPN. VPN gateway IPs need to be whitelisted in our Private Security Groups to allow a secure SSH access from a local client.